In this post, we will look at how to add a Validate-JWT (JSON Web Token) policy to Azure API Management to secure your app services.
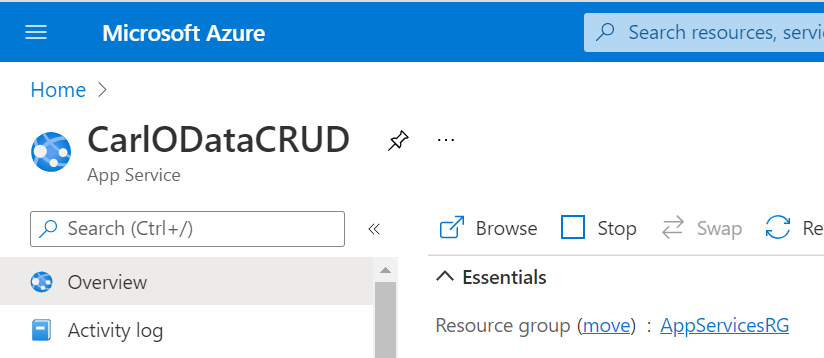
First, let’s look at our setup. We have an Azure App Service called CarlODataCrud:
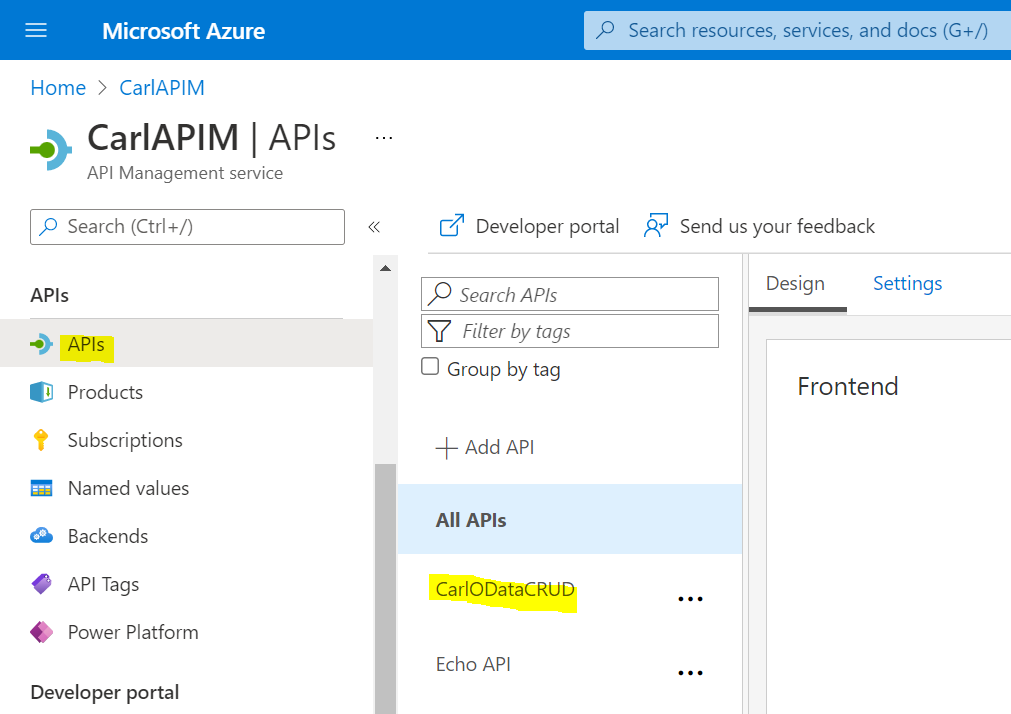
And in Azure API Management we have an API set up that points to this app service:
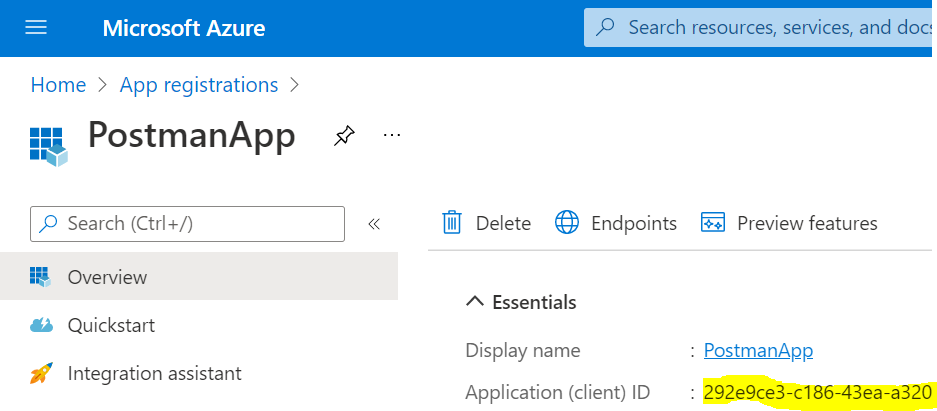
Let’s create an Azure App Registration. You can use an existing App Registration, or create a new one. We will use an existing one – go to App Registrations and copy the Application (Client) Id:
Now, let’s add a validate-jwt policy. We will validate in the header the authorization token is provided. Select All operations, then click on the </> button in the Inbound processing:
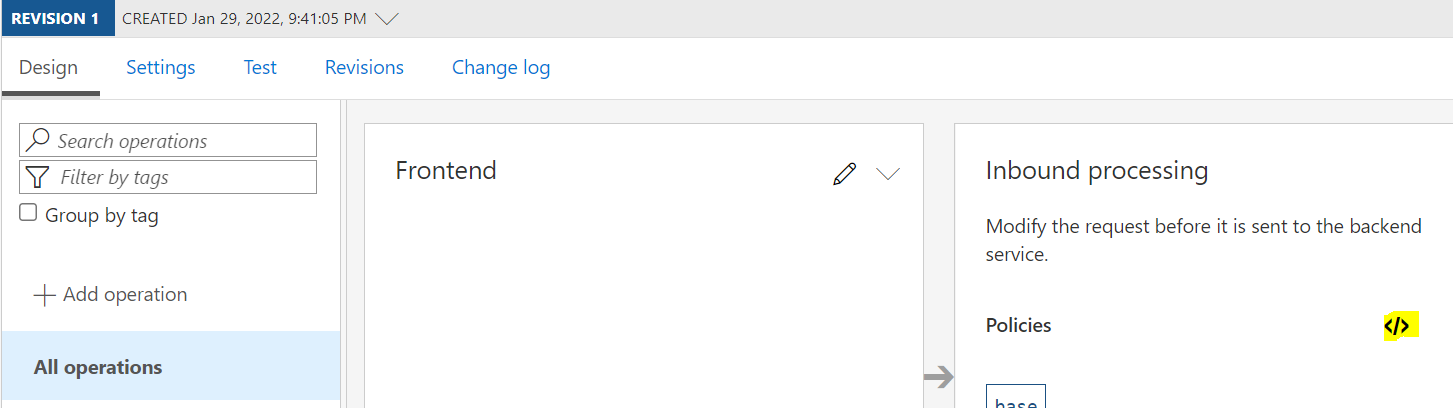
Before we make any changes, the All operations looks like below:

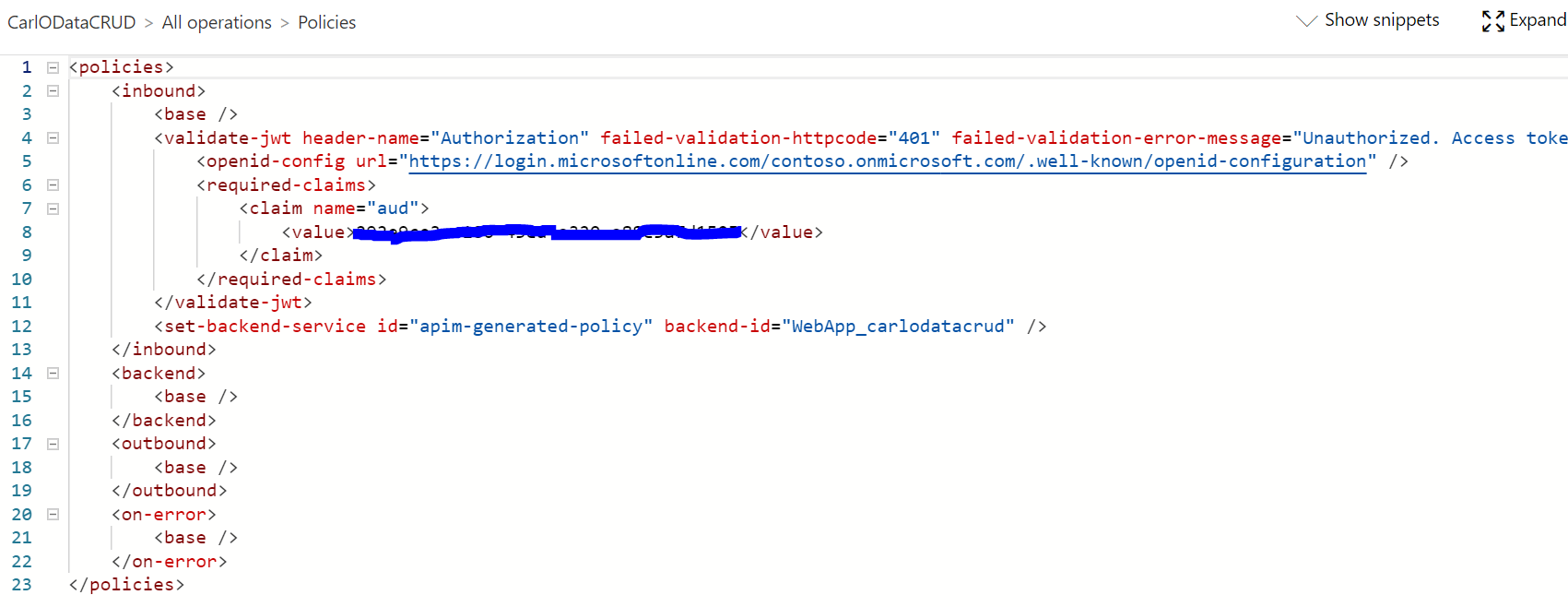
Now let’s add the new policy. We add the validate-jwt token header name = Authorization, and the claim AUD application id (the guid from the Application copied above):
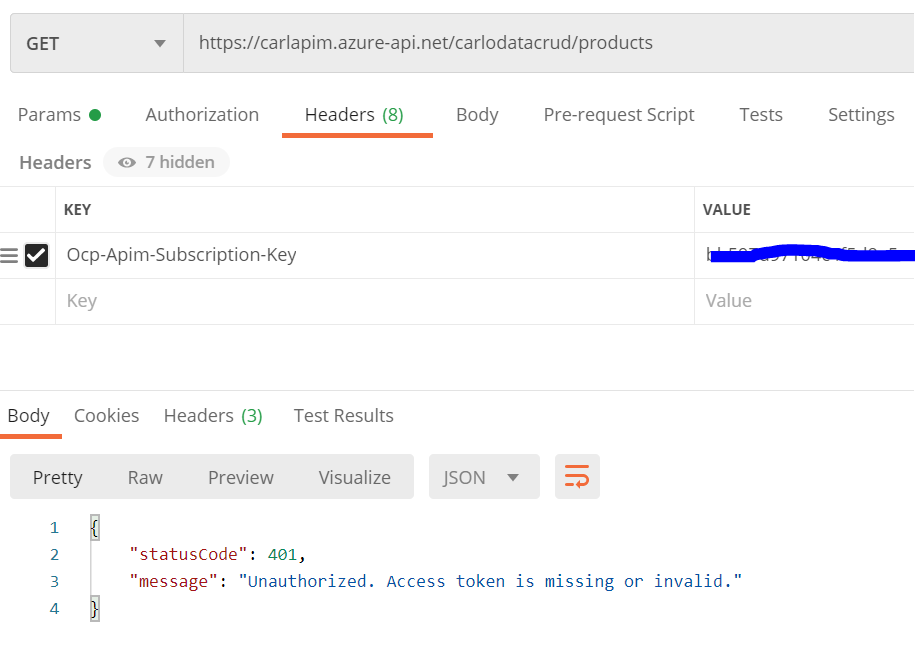
Now let’s run a Postman test. My endpoint requires an Azure Subscription to be provided. If we provide that, and run the test, we get a 401 status, with the message “Unauthorized. Access token is missing or invalid” (previously this worked):
Let’s add an Authorization header. We will need to pass the authorization token, so let’s generate a Bearer token. For the resource, you can use Application Id of the app registration.
Copy the generated bearer token and send it through in the headers with Authorization, Bearer <token>:
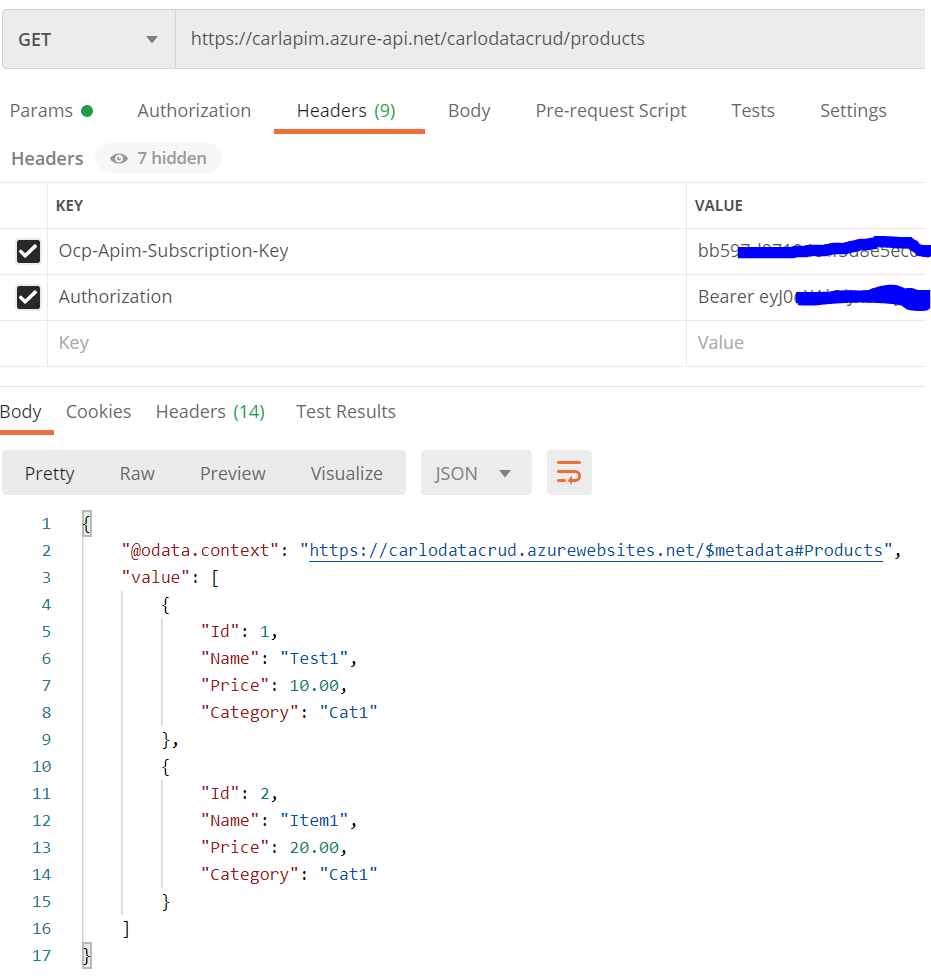
We now get back our 200 response from Azure. If you’re having issues getting this to work, enable Azure Application Insights.
You can read more about Microsoft Identity Platform Access Tokens here.
I AM SPENDING MORE TIME THESE DAYS CREATING YOUTUBE VIDEOS TO HELP PEOPLE LEARN THE MICROSOFT POWER PLATFORM.
IF YOU WOULD LIKE TO SEE HOW I BUILD APPS, OR FIND SOMETHING USEFUL READING MY BLOG, I WOULD REALLY APPRECIATE YOU SUBSCRIBING TO MY YOUTUBE CHANNEL.
THANK YOU, AND LET'S KEEP LEARNING TOGETHER.
CARL

Hi,
I have followed the instructions in this article, but I am getting the below error message, can you please advise?
“message”: “JWT Validation Failed: IDX10500: Signature validation failed. No security keys were provided to validate the signature..”