Let’s look at how to set up conditional multi-factor authentication (MFA) in Azure AD. This is useful if you want to restrict certain users to use MFA in certain apps in your tenant. First, log into https://portal.azure.com and select Azure AD:

Select Security:
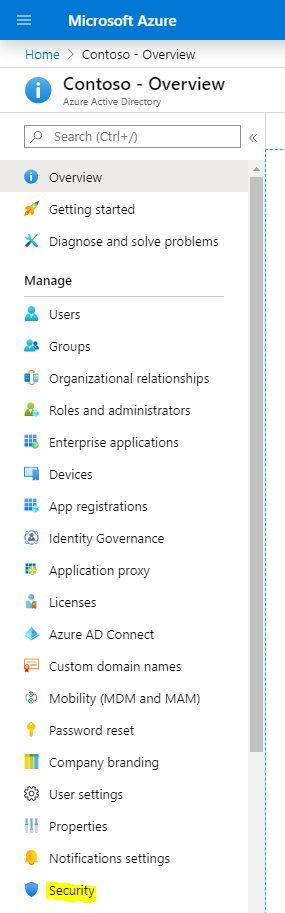
And select Conditional Access:
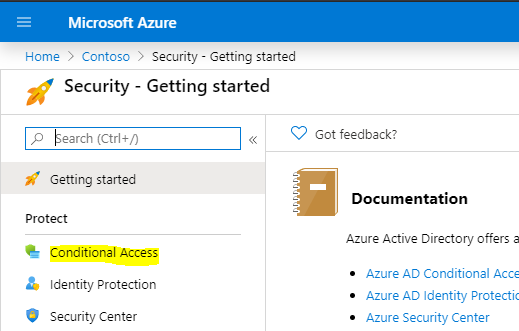
We will create a new policy:
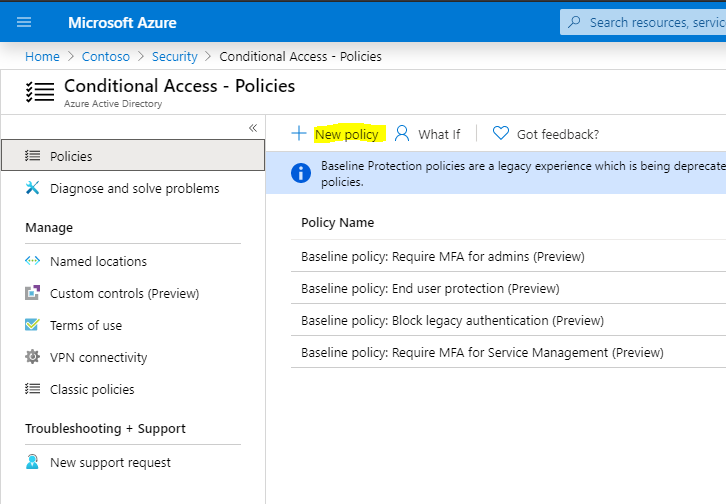
Let’s give it a name, e.g. MFA Conditional Access Policy. We can select to include none, all or a select group of users, and we can select which users are well:
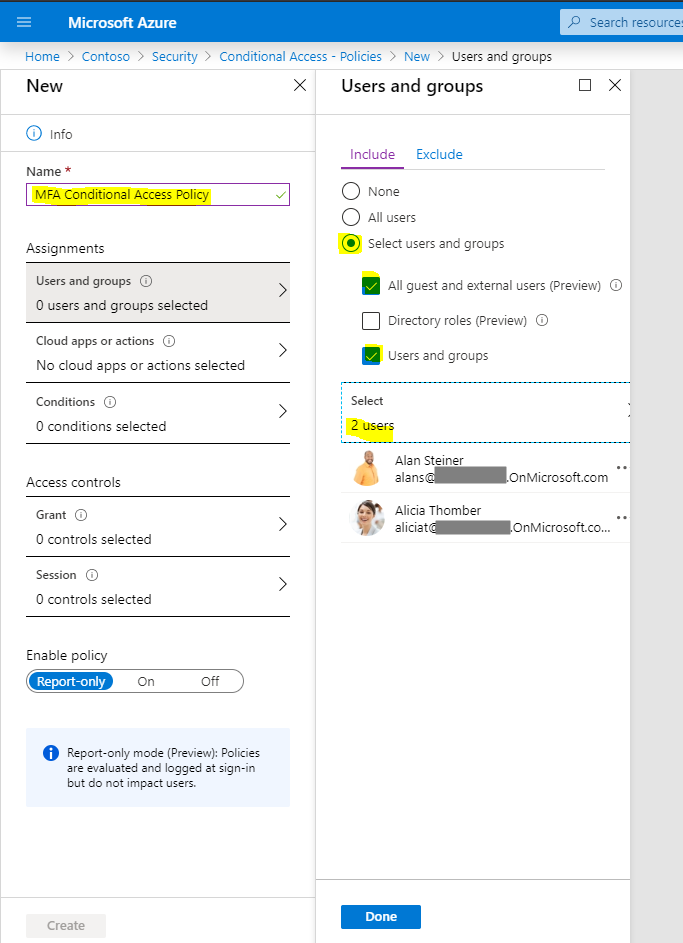
Once selected, let’s choose the apps we want to apply to this policy:
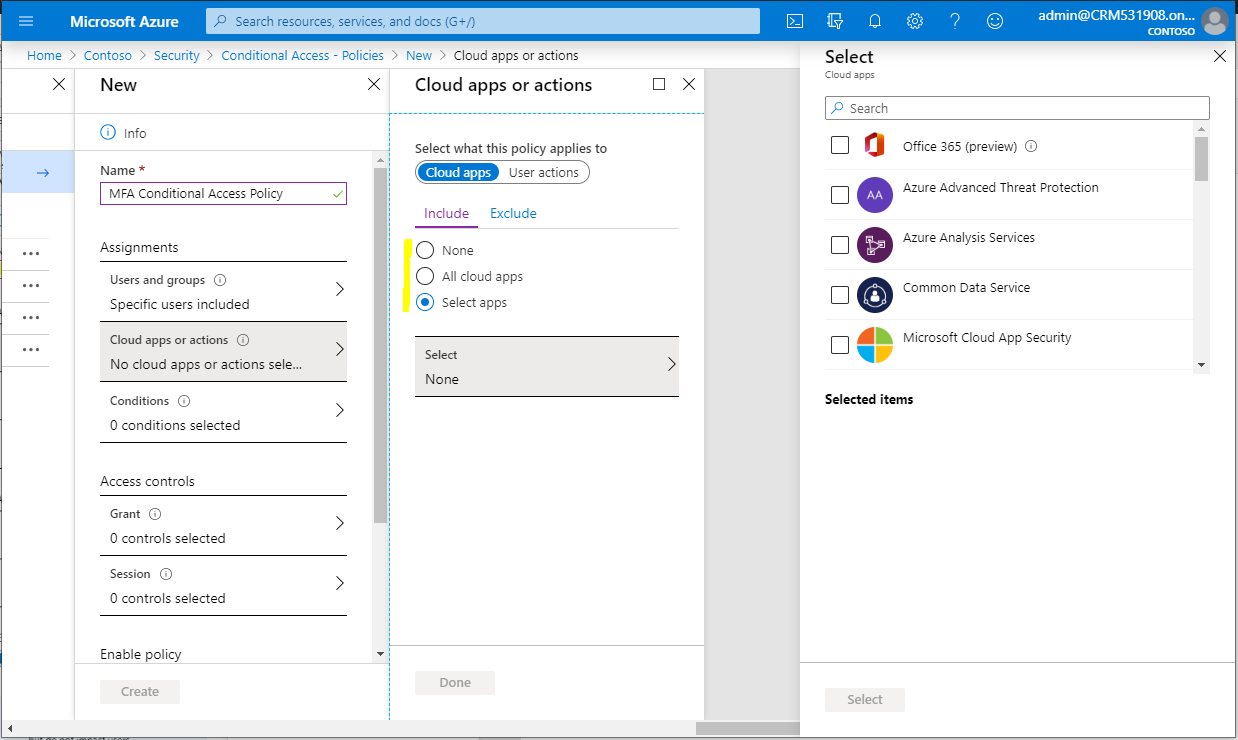
We will select Microsoft Flow:
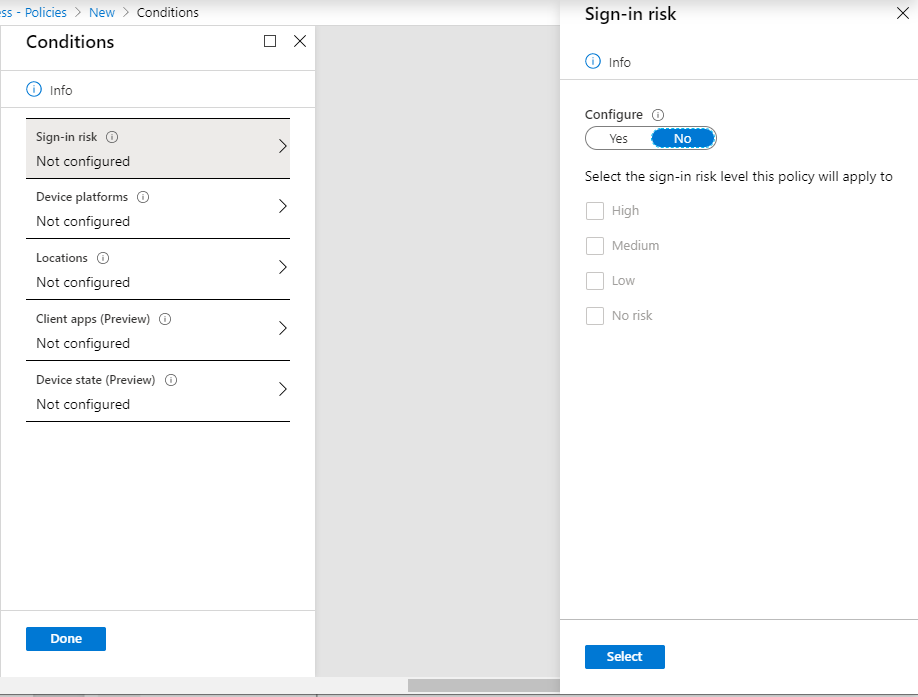
Below are the conditions that can be applied, if required. These include Sign In risk:
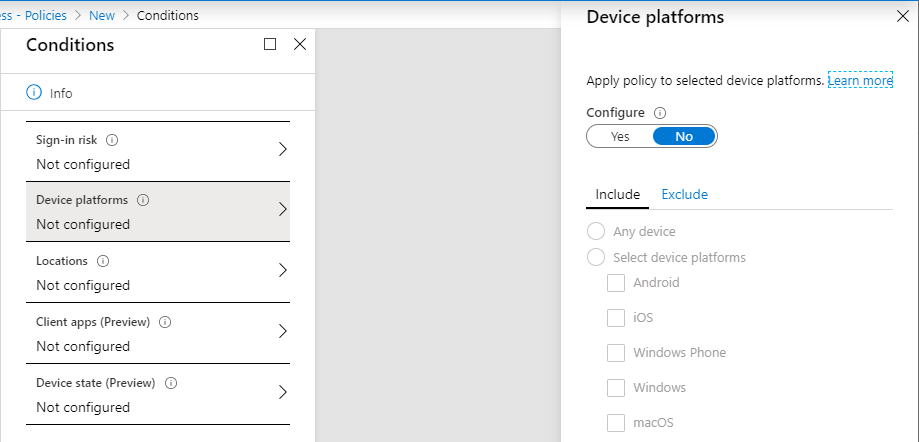
Device Platforms:
Locations:
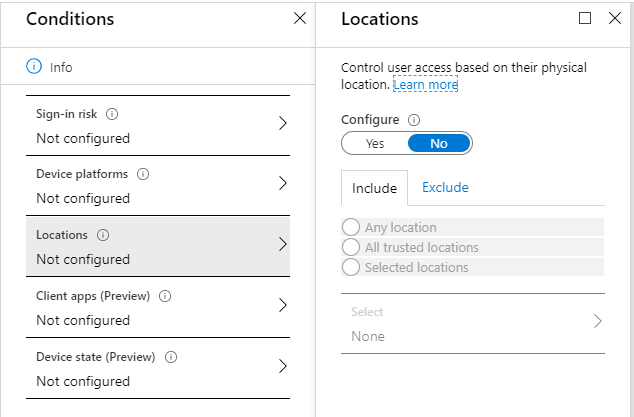
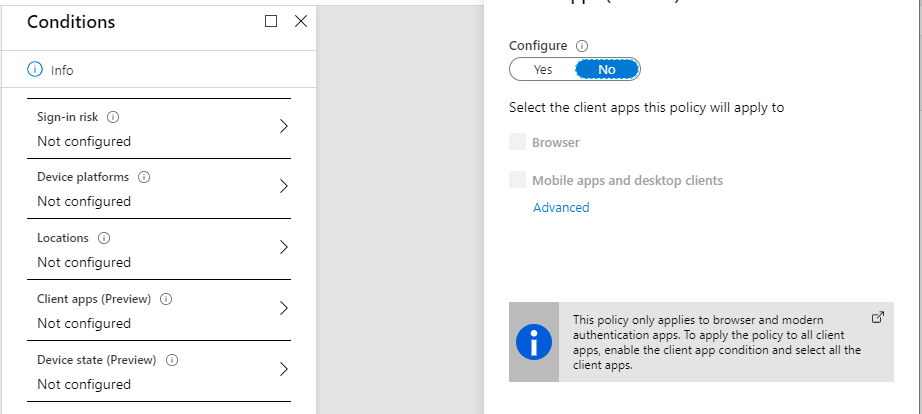
Client apps, such as browser and mobile/desktop apps:
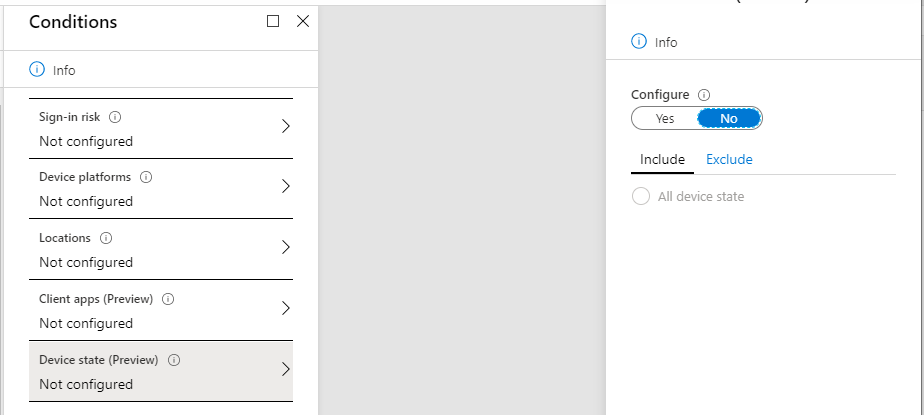
Device state:
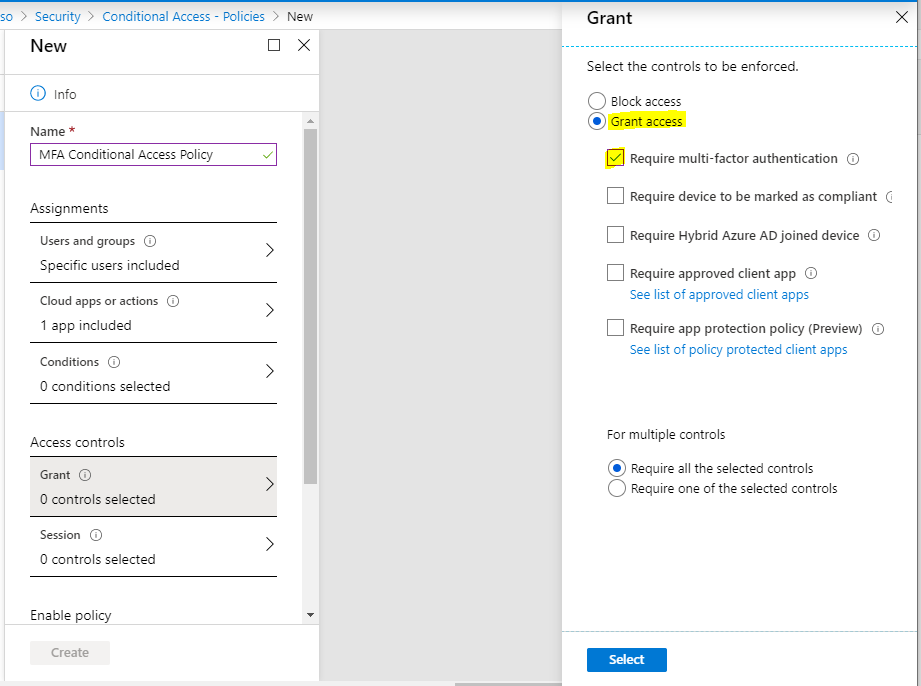
Under Access controls, select to Grant access to require multi-factor authentication:
You can also enable session controls:
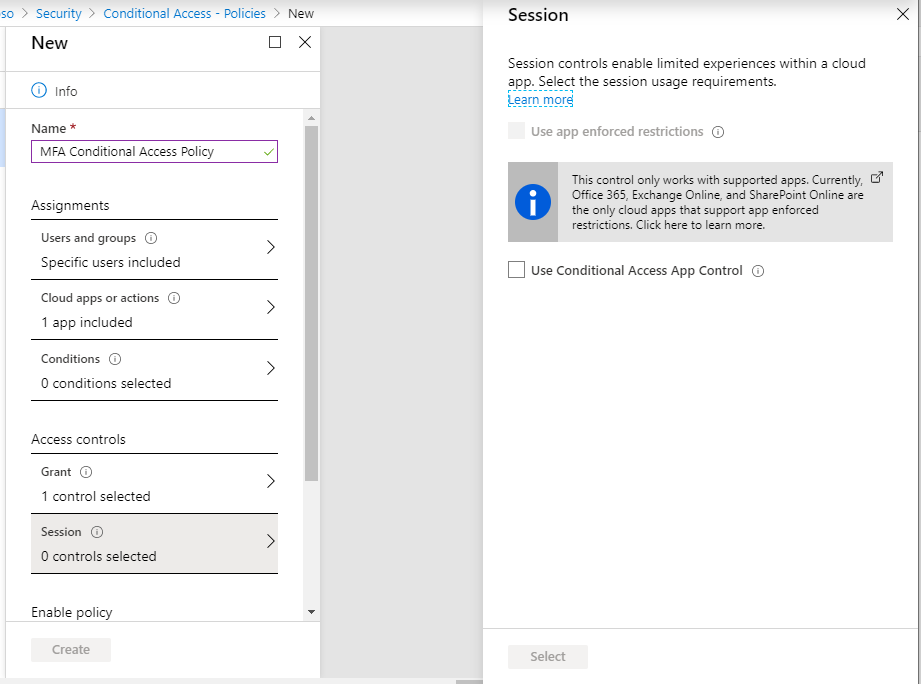
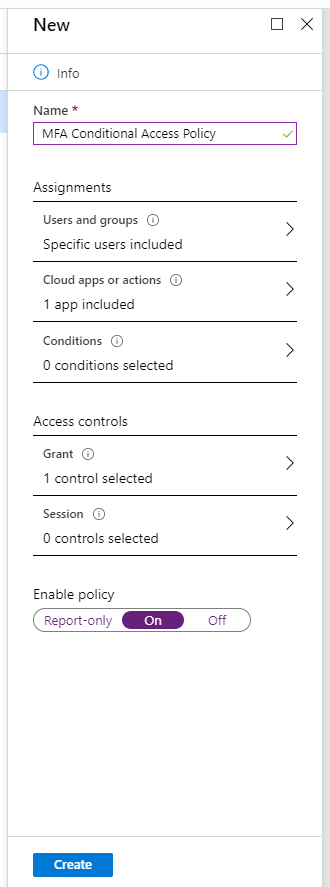
Turn the policy On, and click Create:
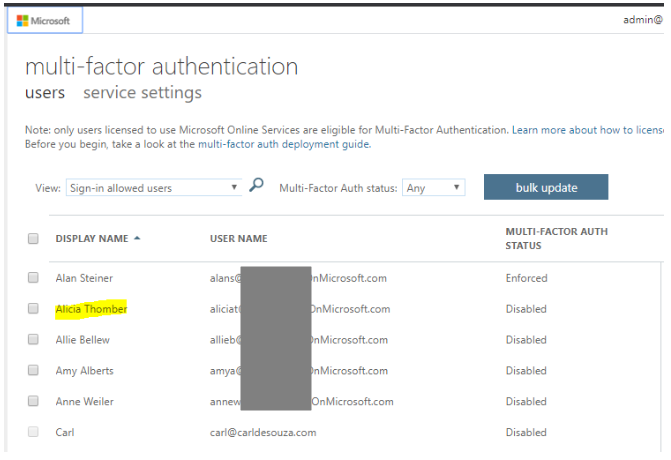
Note that doing this does not globally enable MFA for this user:
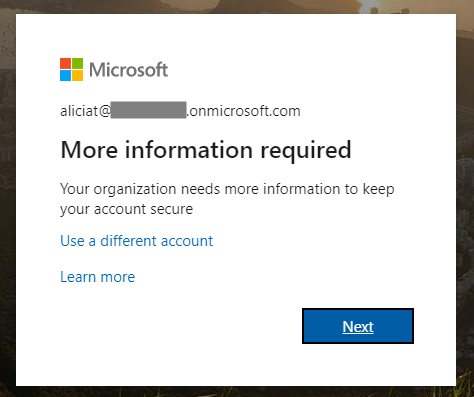
Now let’s test this out. As we enabled this for Power Automate / Flow, let’s log into https://flow.microsoft.com as Alicia. After Alicia enters her username and password, she is prompted for MFA:
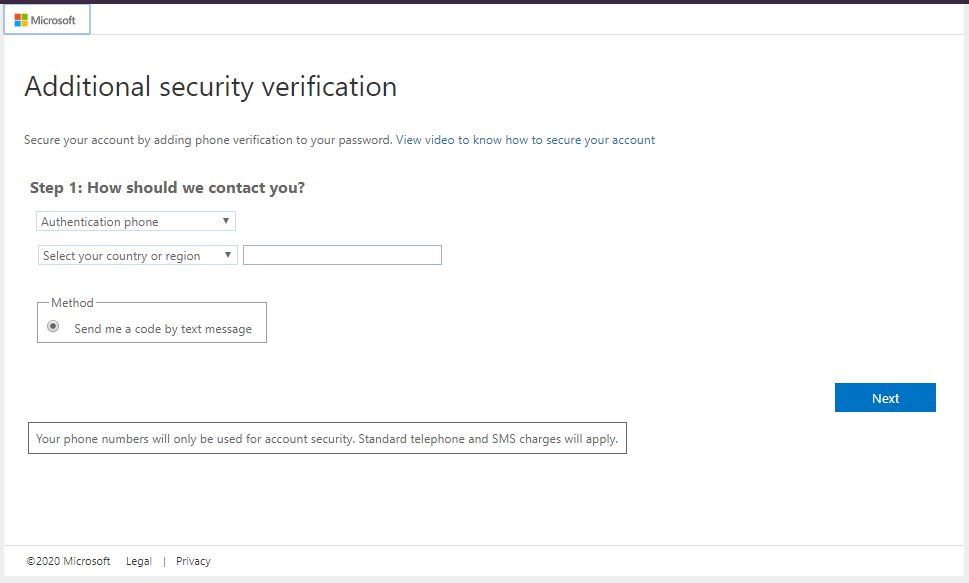
If we logged out of this app, and signed into https://powerbi.com, Alicia would not be prompted for the MFA – she would be prompted for the username and password and then have access to the resource. This is because we don’t have a policy controlling her powerbi.com access:
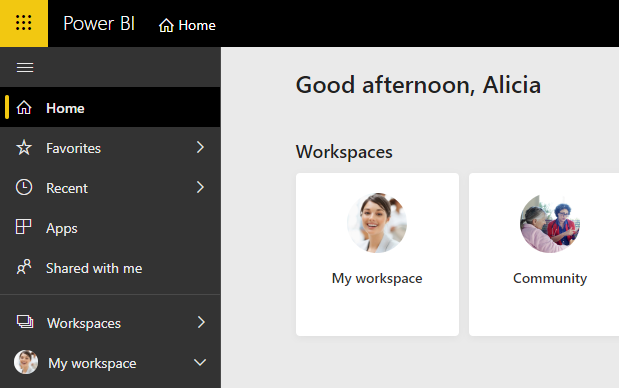
And even once signed in to powerbi.com, if Alicia tries to access flow.microsoft.com, she will run into the MFA check again.
Now let’s look at Guest Access. Let’s say our conditional access policy is now for the Power BI service instead of Flow, and this applies to the Guest User Carl (username carl@carldesouza.com). Now if this user logs into powerbi.com, they will not be prompted for MFA, as they would be taken to their tenant. However, let’s provide them with the organization id (ctid) of our Power BI tenant:
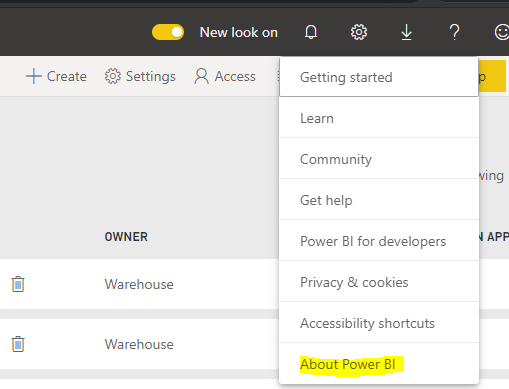
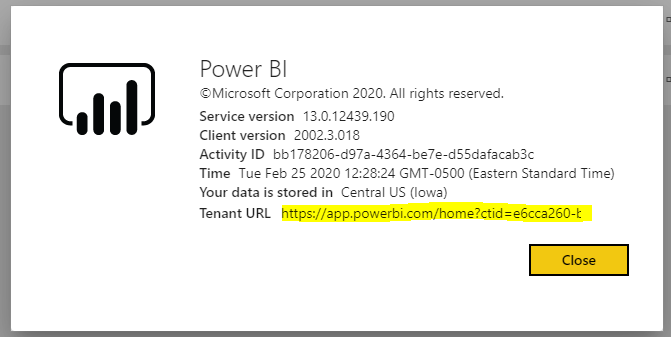
Now when this guest user tries to access this URL, they will be challenged with MFA:
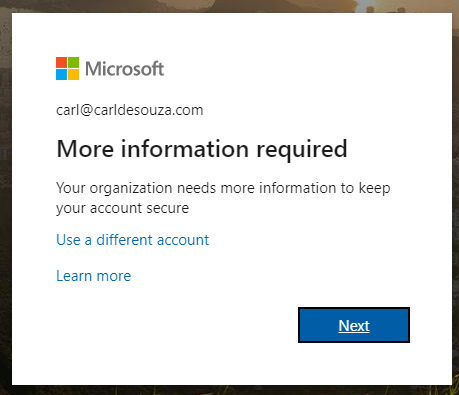
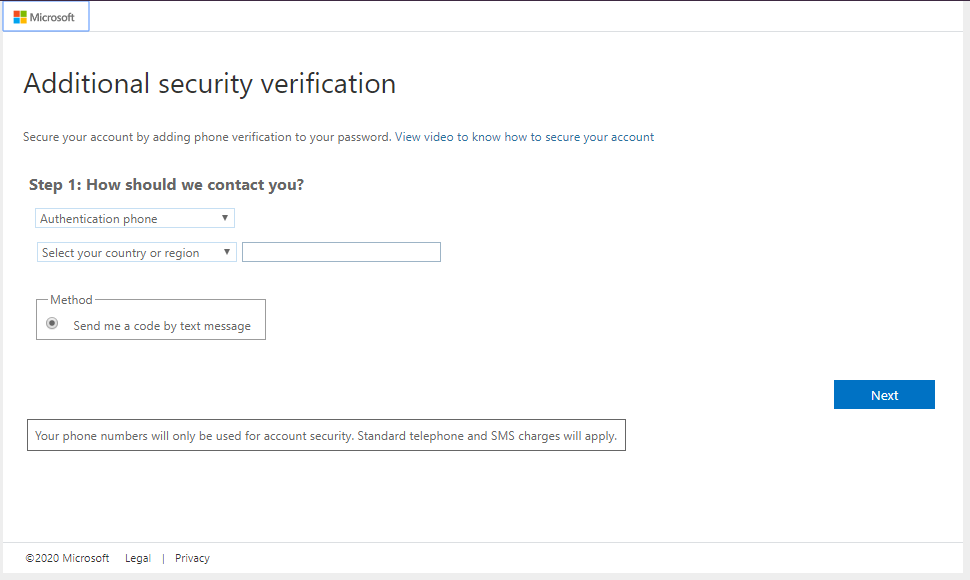
Azure AD has some nice ways to make managing users, security and resources.
I AM SPENDING MORE TIME THESE DAYS CREATING YOUTUBE VIDEOS TO HELP PEOPLE LEARN THE MICROSOFT POWER PLATFORM.
IF YOU WOULD LIKE TO SEE HOW I BUILD APPS, OR FIND SOMETHING USEFUL READING MY BLOG, I WOULD REALLY APPRECIATE YOU SUBSCRIBING TO MY YOUTUBE CHANNEL.
THANK YOU, AND LET'S KEEP LEARNING TOGETHER.
CARL

Hi Carl,
In your example here, you use Flow, which is available in the selector screen when choosing which apps to apply your Conditional Access Policy to. Toward the end, you mention Power BI but my tenant doesn’t appear to have it as a choice. When I’m in the application selector, there is one called “Power BI” but it appears to be a placeholder for an Enterprise Application that has not been setup (if I go to the corresponding Enterprise Application for it, it shows no logins, even though we are heavy users of Power BI). Do you know for sure if this control is available for PBI?