In this post, we will look at how to secure an Azure App Service with authentication by using Azure Active Directory. Go to https://portal.azure.com and select an App Service. We will use one we created earlier. Select Authentication / Authorization:
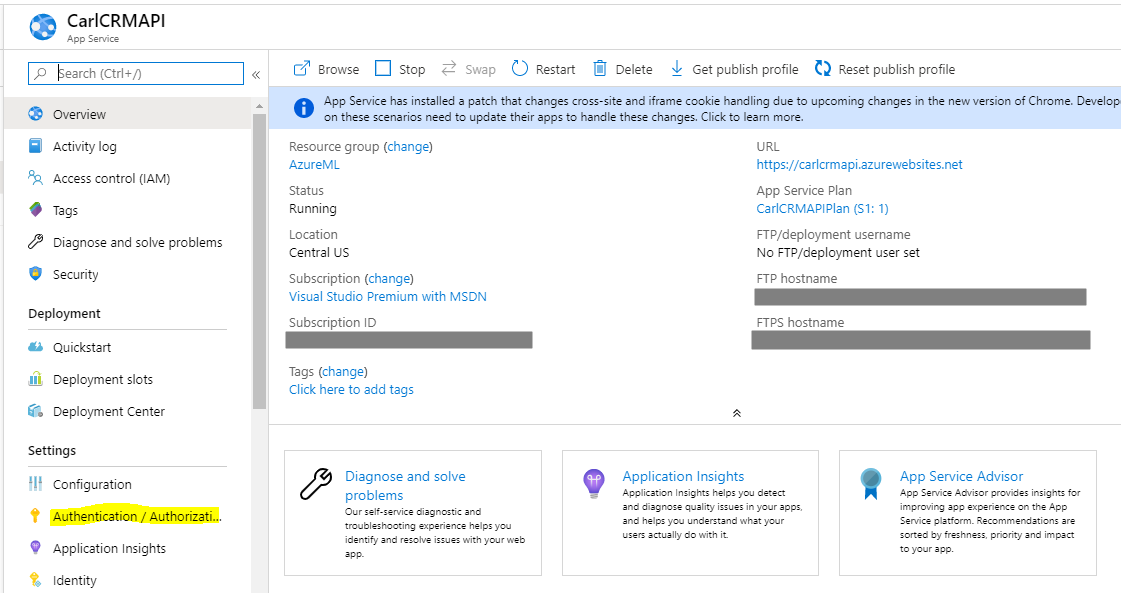
Set App Service Authentication to On:
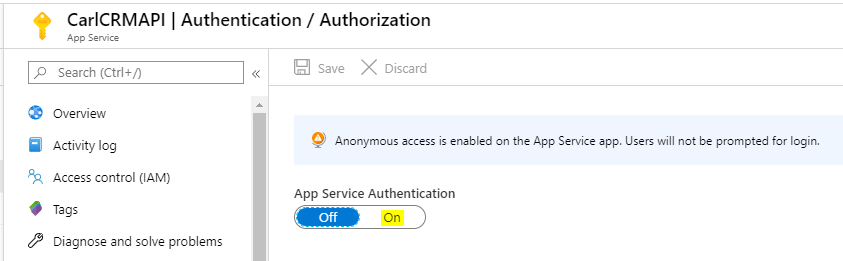
Select Azure Active Directory. Note the other options – Facebook, Google, Twitter etc:
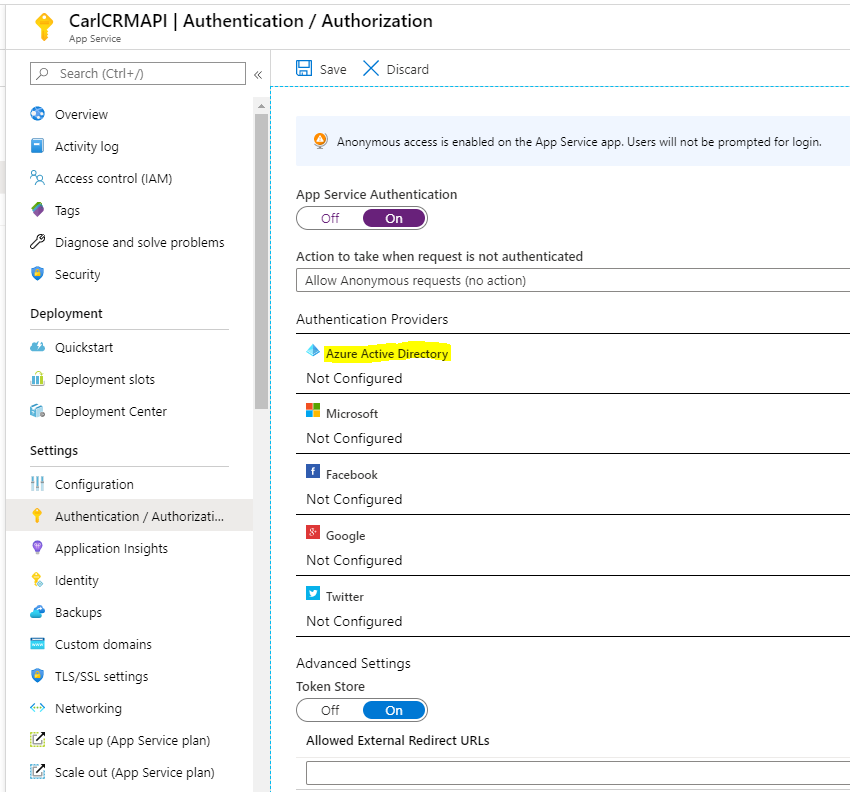
We see:
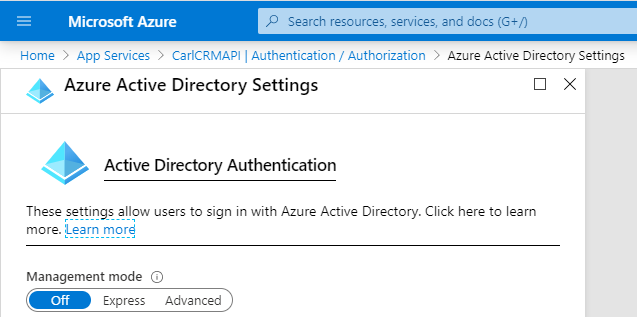
Let’s use Express setup. We will call our app CarlCRMAPIADApp:
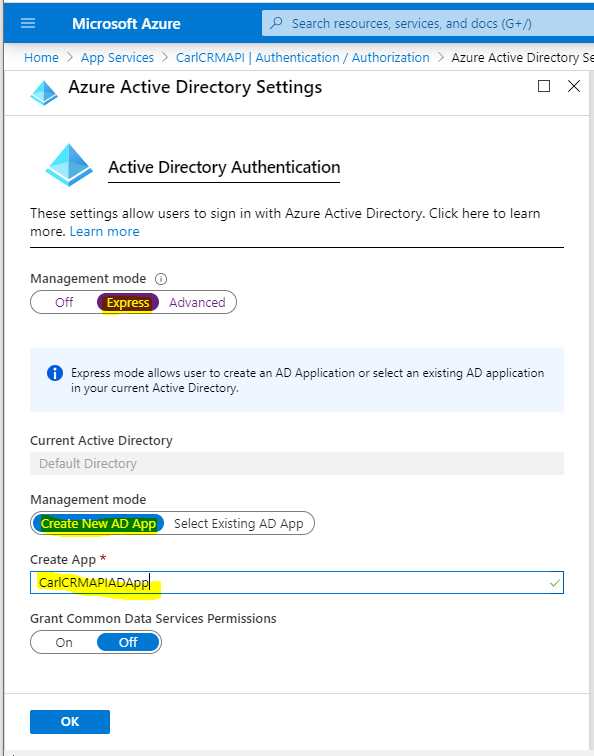
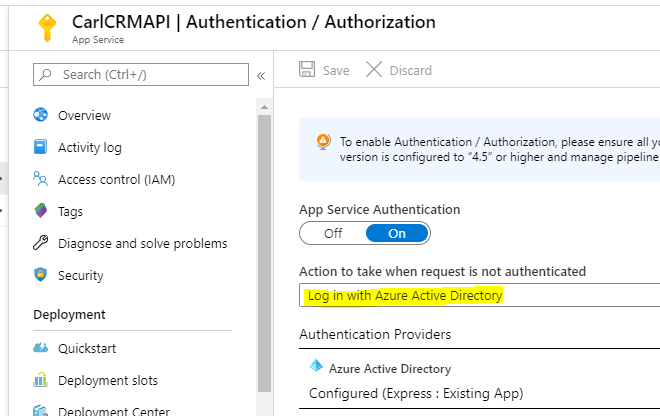
Set Action to take when request is not authenticated = Log in with Azure Active Directory. If you have it set to “Allow Anonymous Requests” then you will still allow these requests to come through, which may not be desired:
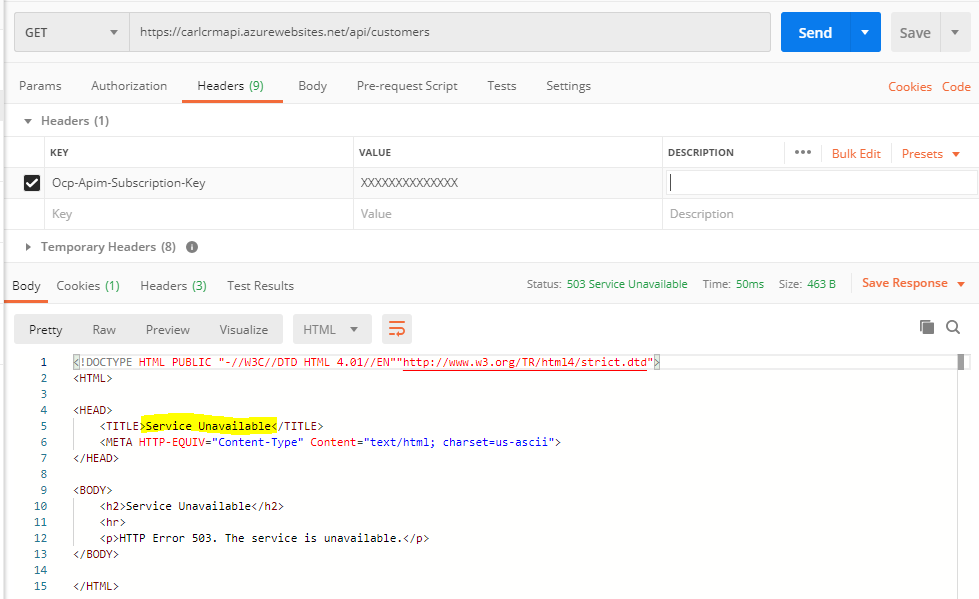
Now, if you send through a request as before, you will get a 503 Service Unavailable error as we are not passing through any authentication:
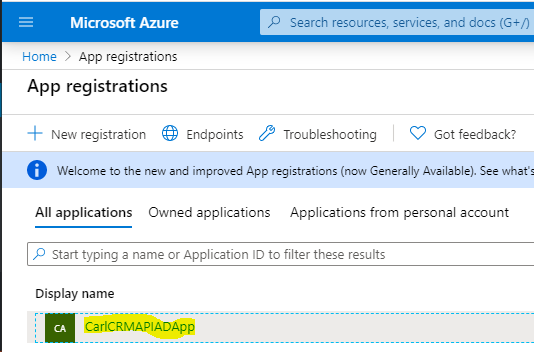
Let’s go to App Registrations and select our App:
Click on Certificates and Secrets. We will create a New Client Secret:
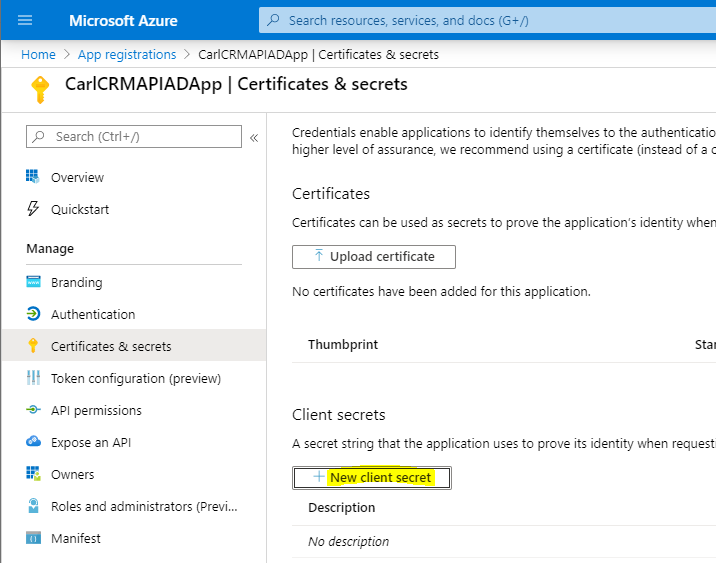
Give the secret a name, and duration:
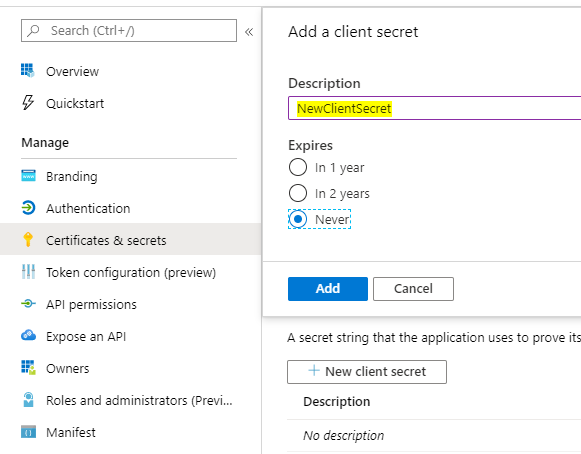
We get a value. Copy it:
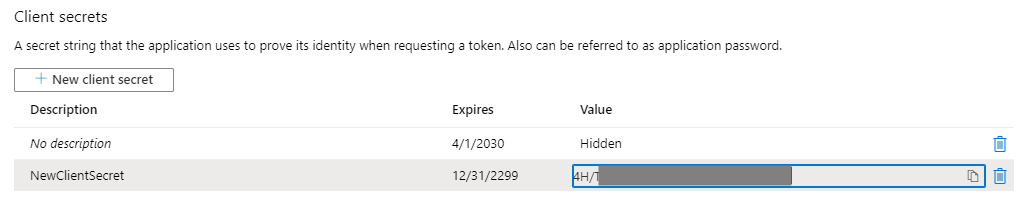
Now in Postman, let’s finish our request. Click the Authorization tab and select OAuth 2.0:

Then Get New Access Token:
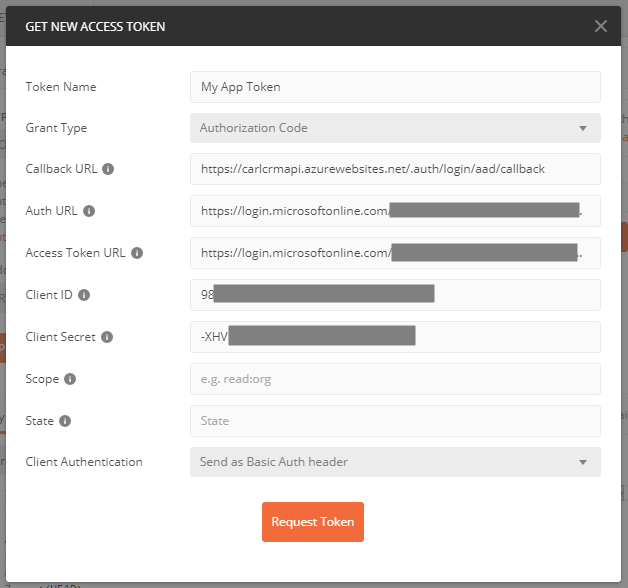
Enter the information below, with information from our App Registration:
Token Name: Anything, e.g. My App Token
Grant Type: Authorization Code
Callback URL: https://carlcrmapi.azurewebsites.net/.auth/login/aad/callback – from Authentication Redirect URL
Auth URL: https://login.microsoftonline.com/directoryid/oauth2/authorize?resource=resourceid where directory id comes from the Overview page of the App Registration and resource id comes from the Overview page Application Id
Access Token URL: https://login.microsoftonline.com/directoryid/oauth2/token?resource=resourceid where directory id comes from the Overview page of the App Registration and resource id comes from the Overview page Application Id
Client Id = from the Overview page of the App Registration the Application Id
Client Secret = Created in Certificates and Secrets
Click Request Token:
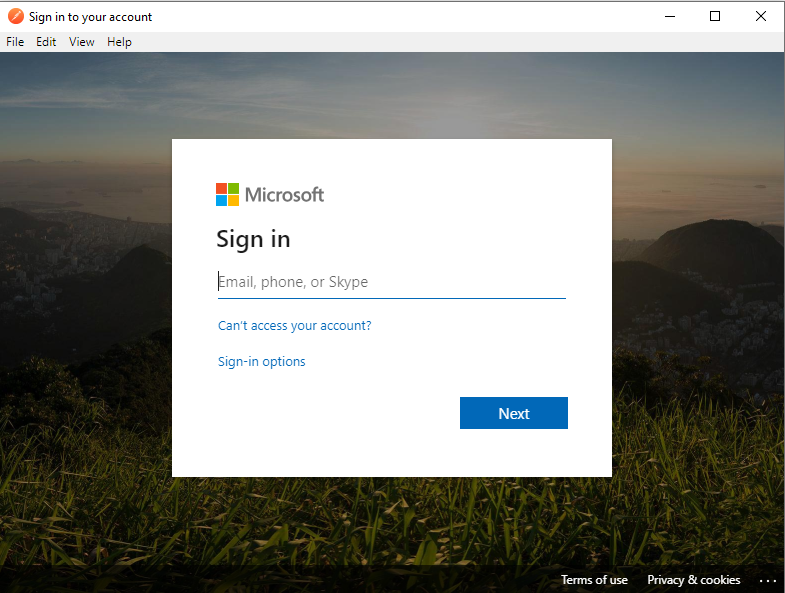
We are prompted to log in:
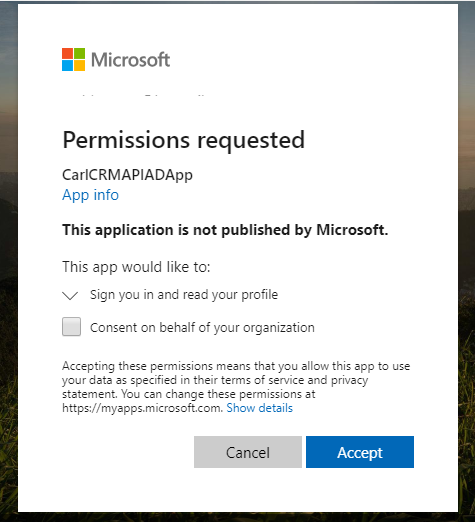
And it asks for permissions. Click Accept:
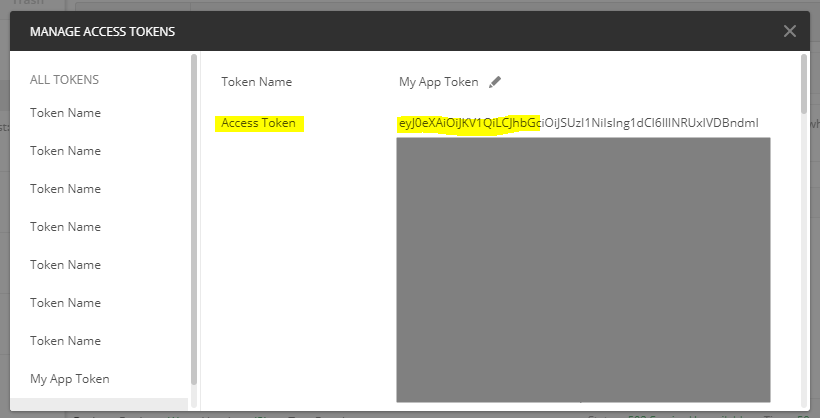
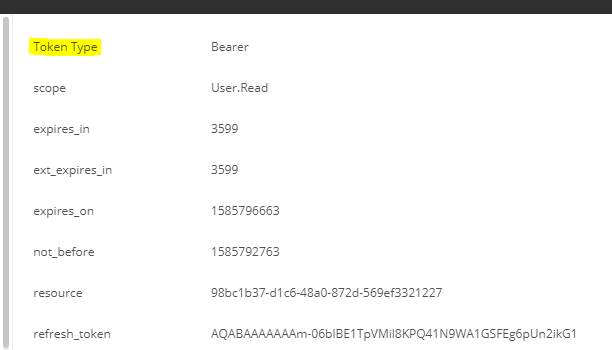
We get an Access Token returned:
Of type Bearer:
Click Use Token:
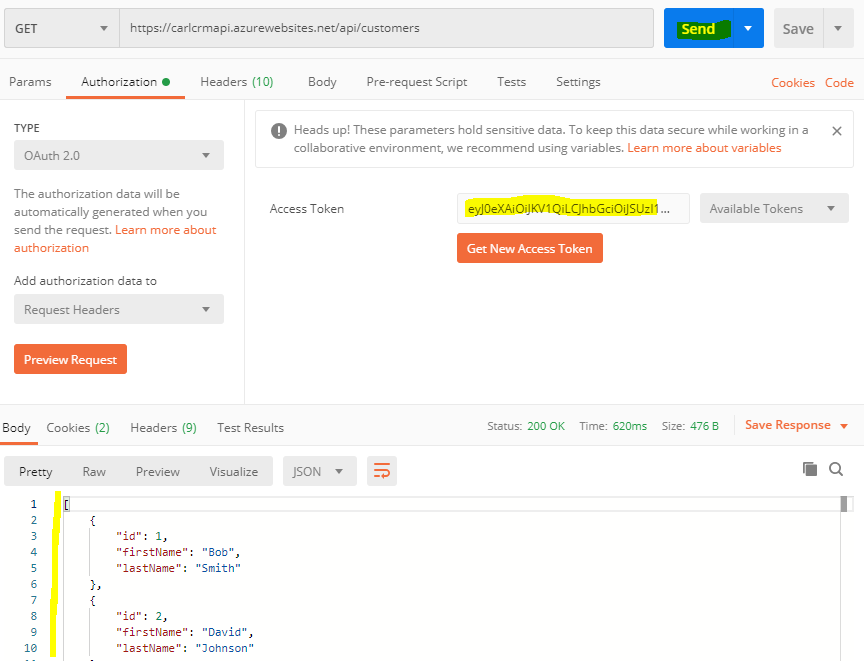
We see the Access Token in the Postman request, with OAuth 2.0 set. Click Send, and we get a response back. We are now authenticated with our app using Azure AD:
I AM SPENDING MORE TIME THESE DAYS CREATING YOUTUBE VIDEOS TO HELP PEOPLE LEARN THE MICROSOFT POWER PLATFORM.
IF YOU WOULD LIKE TO SEE HOW I BUILD APPS, OR FIND SOMETHING USEFUL READING MY BLOG, I WOULD REALLY APPRECIATE YOU SUBSCRIBING TO MY YOUTUBE CHANNEL.
THANK YOU, AND LET'S KEEP LEARNING TOGETHER.
CARL
